
Today’s Cybersecurity Challenge
In the era of digital transformation, the world’s most successful companies lead their industries by monetizing their data and intellectual property. And protecting this data and IP from cyber theft or corruption is critical; losses can devastate profits and hard-earned brand reputations. CISOs and other executives tasked with security understand the stakes but their jobs are harder than ever before in today’s new IT operating model that embraces public clouds, BYOD, and mobility. Data is now everywhere and can be accessed from anywhere.
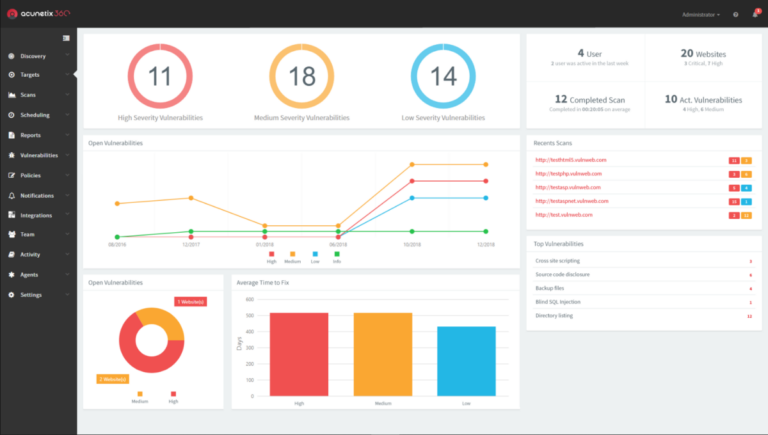
Web Application Security Scanner
As the first company to build a fully dedicated and fully automated web vulnerability scanner, Acunetix carries unparalleled experience in the field and offers a trustworthy all-in-one solution for all your web application security needs.
Acunetix specializes in delivering leading-edge speed and accuracy when it comes to web application security thanks to its unique features, built into the product, so the process of securing your assets falls into the following three steps: FIND. FIX. PREVENT.

Your data is in the cloud. Is your security?
The network perimeter is dissolving. A new perimeter is needed that can protect data and users everywhere, without introducing friction to the business. The Netskope security cloud provides unrivaled visibility and real-time data and threat protection when accessing cloud services, websites, and private apps from anywhere, on any device. Only Netskope understands the cloud and delivers data-centric security from one of the world’s largest and fastest security networks, empowering the largest organizations in the world with the right balance of protection and speed they need to enable business velocity and secure their digital transformation journey.
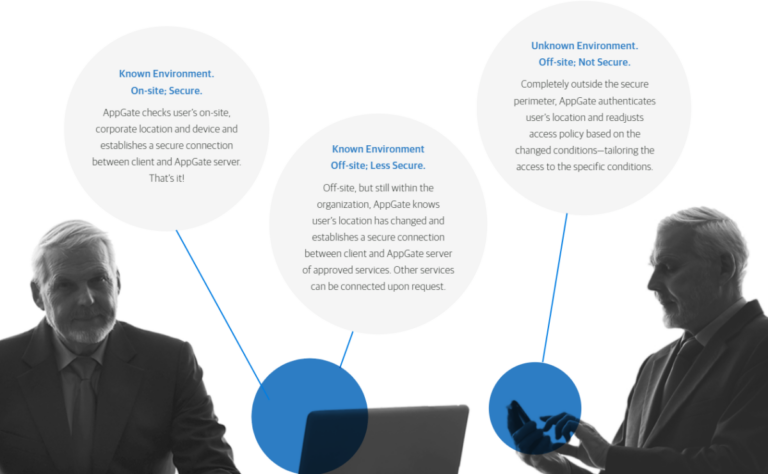
Context Aware, Secure Access Gateway Connects Users, Apps and Services
The growth of enterprise collaboration, consumption of information on personal devices and mobile distributed workers has resulted in the collapse of the traditional network. Today, users require access to business applications, data and services whether at work or on the road. And in today’s globally connected business environment, those users could be employees, partners or customers.
Identity management for all your people, all your devices, and all your applications.
In the last decade, enterprises everywhere have embraced cloud apps like Salesforce.com, and NetSuite; GoToMeeting and WebEx; and Workday and SuccessFactors. They’ve shrunk their IT infrastructure, lowered their total cost of ownership, and made it possible for employees to get work done anywhere, at any hour.
But the change hasn’t come easy. IT departments still have to manage all of their on-premises apps and infrastructure, only now it is more difficult because they lack a single view of all users, apps, and devices. What is needed is a common identity platform to connect the enterprise. By choosing Okta, companies are solving the challenges that have been created by new cloud and mobile technologies and are preparing themselves to meet the next wave of innovation.

ServiceNow delivers digital workflows that create great experiences and unlock productivity.
ServiceNow reports non-GAAP results in addition to, and not as a substitute for, or superior to, financial measures calculated in accordance with GAAP. To see the reconciliation between these non-GAAP and GAAP results, please refer to our earnings release issued on April 29, 2020, and, for prior periods, previously filed earnings releases, all of which are available at investors.servicenow.com.
Code42 Security Tools
Threats to data from inside the organization can happen accidentally when employees make mistakes or lose their laptops, or maliciously when employees intentionally steal, sell or sabotage data—but both behaviors can result in operational, financial or reputational harm to an organization.


SEE YOUR NETWORK THROUGH THE EYES OF A HACKER
A dedicated hacker is going to evaluate your security measures and find ways around them. The question is what happens after they breach your perimeter.
XM Cyber gives you the ability to see your network the way the hacker sees it. It helps you to find all existing hidden vectors of attack, including those that typically go under the radar of most protective measures. And once an attack path is identified, XM Cyber delivers a focused and prioritized remediation report so you can fix those weaknesses before the hacker strikes.
Our patented approach helps you reduce your risk by exposing gaps resulting from unpatched systems, misconfigurations, software flaws and human error. Regardless of your security controls, if there exists an attack vector that through any means can reach your critical assets, XM Cyber will find it.
